Help your clients stay one step ahead of cyber threats
Phishing Campaign Scheduler
- Choose Your Campaign
Select one of this quarter’s templates below — or work with your customer to choose what’s most relevant. - Complete the Form
Enter your campaign details, including preferred launch window, customer name, and selected template. - Receive Whitelisting Instructions
We’ll send you the whitelisting steps to ensure smooth delivery — no inbox disruptions. - Confirm Setup
Once confirmed, we’ll send a test email to verify the look, feel, and inbox appearance. - Campaign Launch
We’ll schedule and deliver the campaign, typically over 1–3 days, with a 1-week tracking window. - Receive Your Report
After completion, you’ll receive a partner-branded report and an Excel breakdown of user-level results.
This Quarter's Featured Phishing Scenarios
- DocuSign
- Sharepoint
- Microsoft Teams
- QR Code
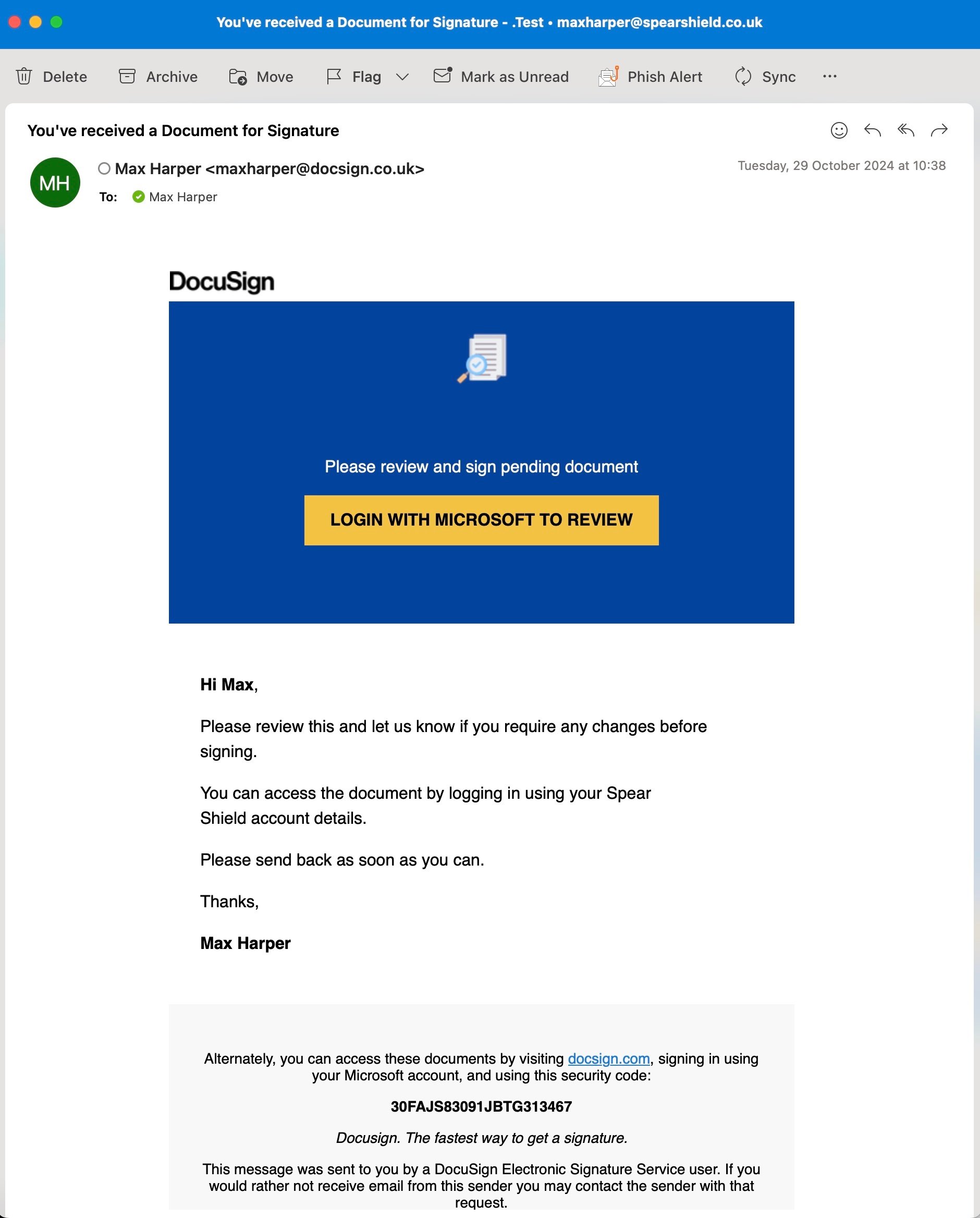
DocuSign Impersonation
Why this template works well
1. Familiar Branding & Design
-
It convincingly mimics a DocuSign notification, a trusted and widely-used platform.
-
The layout, logo, and call-to-action (CTA) closely resemble legitimate DocuSign emails, which increases the likelihood of user interaction.
2. High Relevance in Real-World Attacks
-
DocuSign-themed phishing is common in real attack campaigns, especially targeting finance, legal, and HR teams — making this simulation directly relevant to actual threats.
3. Strong Call to Action
-
The button, "LOGIN WITH MICROSOFT TO REVIEW", introduces a dual impersonation vector (DocuSign and Microsoft), which attackers often use to steal login credentials — this dual lure boosts realism.
4. Subtle Red Flags
-
While convincing, the email contains minor discrepancies that trained users could spot:
-
Sender address (
maxharper@docusign.co.uk) is suspicious. -
Mixed branding (DocuSign + Microsoft login) might raise doubts.
-
Slightly generic language and a sense of urgency (“Please send back as soon as you can”).
-
This makes it perfect for awareness training — users can learn to identify these subtle clues in a safe environment.
DocuSign Impersonation
Why this template works well
1. Familiar Branding & Design
-
It convincingly mimics a DocuSign notification, a trusted and widely-used platform.
-
The layout, logo, and call-to-action (CTA) closely resemble legitimate DocuSign emails, which increases the likelihood of user interaction.
2. High Relevance in Real-World Attacks
-
DocuSign-themed phishing is common in real attack campaigns, especially targeting finance, legal, and HR teams — making this simulation directly relevant to actual threats.
3. Strong Call to Action
-
The button, "LOGIN WITH MICROSOFT TO REVIEW", introduces a dual impersonation vector (DocuSign and Microsoft), which attackers often use to steal login credentials — this dual lure boosts realism.
4. Subtle Red Flags
-
While convincing, the email contains minor discrepancies that trained users could spot:
-
Sender address (
maxharper@docusign.co.uk) is suspicious. -
Mixed branding (DocuSign + Microsoft login) might raise doubts.
-
Slightly generic language and a sense of urgency (“Please send back as soon as you can”).
-
This makes it perfect for awareness training — users can learn to identify these subtle clues in a safe environment.

DocuSign Impersonation
Why this template works well
1. Familiar Branding & Design
-
It convincingly mimics a DocuSign notification, a trusted and widely-used platform.
-
The layout, logo, and call-to-action (CTA) closely resemble legitimate DocuSign emails, which increases the likelihood of user interaction.
2. High Relevance in Real-World Attacks
-
DocuSign-themed phishing is common in real attack campaigns, especially targeting finance, legal, and HR teams — making this simulation directly relevant to actual threats.
3. Strong Call to Action
-
The button, "LOGIN WITH MICROSOFT TO REVIEW", introduces a dual impersonation vector (DocuSign and Microsoft), which attackers often use to steal login credentials — this dual lure boosts realism.
4. Subtle Red Flags
-
While convincing, the email contains minor discrepancies that trained users could spot:
-
Sender address (
maxharper@docusign.co.uk) is suspicious. -
Mixed branding (DocuSign + Microsoft login) might raise doubts.
-
Slightly generic language and a sense of urgency (“Please send back as soon as you can”).
-
This makes it perfect for awareness training — users can learn to identify these subtle clues in a safe environment.

DocuSign Impersonation
Why this template works well
1. Familiar Branding & Design
-
It convincingly mimics a DocuSign notification, a trusted and widely-used platform.
-
The layout, logo, and call-to-action (CTA) closely resemble legitimate DocuSign emails, which increases the likelihood of user interaction.
2. High Relevance in Real-World Attacks
-
DocuSign-themed phishing is common in real attack campaigns, especially targeting finance, legal, and HR teams — making this simulation directly relevant to actual threats.
3. Strong Call to Action
-
The button, "LOGIN WITH MICROSOFT TO REVIEW", introduces a dual impersonation vector (DocuSign and Microsoft), which attackers often use to steal login credentials — this dual lure boosts realism.
4. Subtle Red Flags
-
While convincing, the email contains minor discrepancies that trained users could spot:
-
Sender address (
maxharper@docusign.co.uk) is suspicious. -
Mixed branding (DocuSign + Microsoft login) might raise doubts.
-
Slightly generic language and a sense of urgency (“Please send back as soon as you can”).
-
This makes it perfect for awareness training — users can learn to identify these subtle clues in a safe environment.

Campaign Booking Form
Let us know your chosen template and launch details"GAIN INSIGHT INTO RISK AND USERS SECURITY BEHAVIOURS"
 "Phishing is the most effective attack vector for cybercriminals, yet too many businesses rely on off-the-shelf phishing templates that don’t reflect real-world threats. At Spear Shield, we take a spear phishing approach, crafting highly targeted simulations that mimic the tactics we see attackers using in the wild.
"Phishing is the most effective attack vector for cybercriminals, yet too many businesses rely on off-the-shelf phishing templates that don’t reflect real-world threats. At Spear Shield, we take a spear phishing approach, crafting highly targeted simulations that mimic the tactics we see attackers using in the wild.
Running a phishing campaign isn’t just about seeing who clicks - it’s about understanding user behaviours, identifying real risks, and providing actionable insights that you and your customers can articulate back to their business. With fully branded reporting and associated caught-user breakdown, you’ll gain a clear picture of your customer’s resilience to phishing attacks.
Josh Broadbent, CTO, Spear Shield
HUMAN RISK LANSCAPE
WHY DO YOUR CUSTOMERS NEED TO BE RUNNING PHISHING SIMULATIONS?
- Slipping through the net
In 2024, there was a 52.2% increase in the number of attacks that got through Secure Email Gateway (SEG) detection and a 50.9% increase in attacks bypassing Microsoft’s native defences. - It started with a Phish...
61% of the root cause of ransomware attacks responded to in 2024 was introduced to an organisation through ‘human-activated risk’. Compromised credentials, malicious emails, phishing, downloads and more. -
Less than 60 seconds
The Median time to click on a malicious link after the email is opened is 21 seconds and then only another 28 seconds for the person caught in the phishing scheme to enter their data. The median time for users to fall for phishing emails is less than 60 seconds.
.png?width=2144&height=2252&name=Copy%20of%20SSS%20ITFC%20Nov%202024%20Promo%20(22).png)
YOU MAY NEED TO KNOW
Frequently Asked Questions
Can’t we just run phishing simulations ourselves?
You could — but the difference is in the delivery. We remove all the guesswork, vet every click to exclude false positives like scanners and bots, and present the results clearly. No manual data cleaning, no missed insights — just real human behaviour, accurately measured.
We already have a phishing platform — why use this service?
Having a platform is one thing. Using it effectively is another. You’d still need to scope clients, pick relevant templates, manage whitelisting, and build reports. With Spear Shield, you get expert-curated campaigns built around what’s actually bypassing email defences — all fully managed, and branded to you.
Do we need to manage anything?
Just the relationship with your customer. We take care of the rest — including scheduling, running, monitoring, and reporting. You don’t need any technical resources or experience. Just book it in and we’ll deliver.
How much time does this take to manage?
Very little. You simply pick a campaign, fill out a form, and we handle everything else — including whitelisting guidance, delivery, tracking, and reporting. It’s designed to scale without adding to your workload.
Can I brand it for my customers?
Yes — everything we send can be branded to your business. Reports, training pages, and communication touchpoints can carry your logo and tone, helping you stay front-of-mind with your customers.
Will users get annoyed by these tests?
Not at all. Our simulations are designed to mimic real threats without disruption. If a user clicks, they’re taken to a branded training page — no lectures, no public call-outs. Just clear, constructive feedback in the moment that matters most.
What types of phishing attacks can you simulate?
We include a wide range of relevant, real-world templates as standard. However, if your customer wants something bespoke — such as a scenario tailored to a specific brand, process, or department — we can build a custom Spear Phish Pack for a one-off fee of £100.
What about data privacy and GDPR compliance?
We take data privacy seriously. We only process email addresses and store reporting data to track user performance over time. We do not store passwords or credentials — even if a user attempts to submit them. We simply log whether a submission occurred, with no visibility of the entered content. All data is handled securely in line with GDPR requirements.
I'm not a partner yet — how can I become one?
It’s easy. Just reach out to us at hello@spearshield.co.uk or visit our contact us page on our website to get started. We’ll provide everything you need to launch, including onboarding support and access to our campaign scheduler. There are no long-term contracts or minimum commitments — just a flexible, fully managed service you can sell under your own brand.
RECENTLY SHARED
The Spear Blog

Company News Max Harper 14-Jan-2026 15:57:55 6 min read
Spear Shield and Koncise Company Announcement

Email Security Managed Phishing Human Risk Social Engineering Max Harper 20-Nov-2025 17:11:06 13 min read
The Meeting That Bites: Calendar-Invite Phishing Explained
Email Security Managed Phishing Human Risk Social Engineering Max Harper 03-Nov-2025 15:04:30 10 min read