Rescued by Egress Defend - Account Takeover that left heads scratching
Email Security 14-Dec-2022 15:57:21 Max Harper 5 min read

"Wait a minute..."
~ Users at Spear Shield.
As a business whose sole focus is cybersecurity - all of our users back their abilities to spot phishing attempts with their eyes closed! (not literally... but you get the point we're trying to make.) but this one left all of us double guessing and scratching our heads..!
The Background...
The team at Spear Shield attend many networking events throughout the year. It is not uncommon for us to make a connection with another business and depending on the different services provided, make recommendations to the customers we work with "oh yeah, we know a person for that" and it works vice-versa - "cybersecurity you say? have you met...... the Spears!"
So when the team all received an email yesterday from a known contact, at first glance, it was just your usual email. But let's take a closer look...
Warning sign number 1.
The big red banner!
We use Egress Defend as an Integrated Cloud Email Security (ICES) tool internally that provides our users with real-time teachable moments - as demonstrated with the dynamic HTML banners in the email below.
But this must be a false positive right? We usually communicate with X.
Here's what went down:
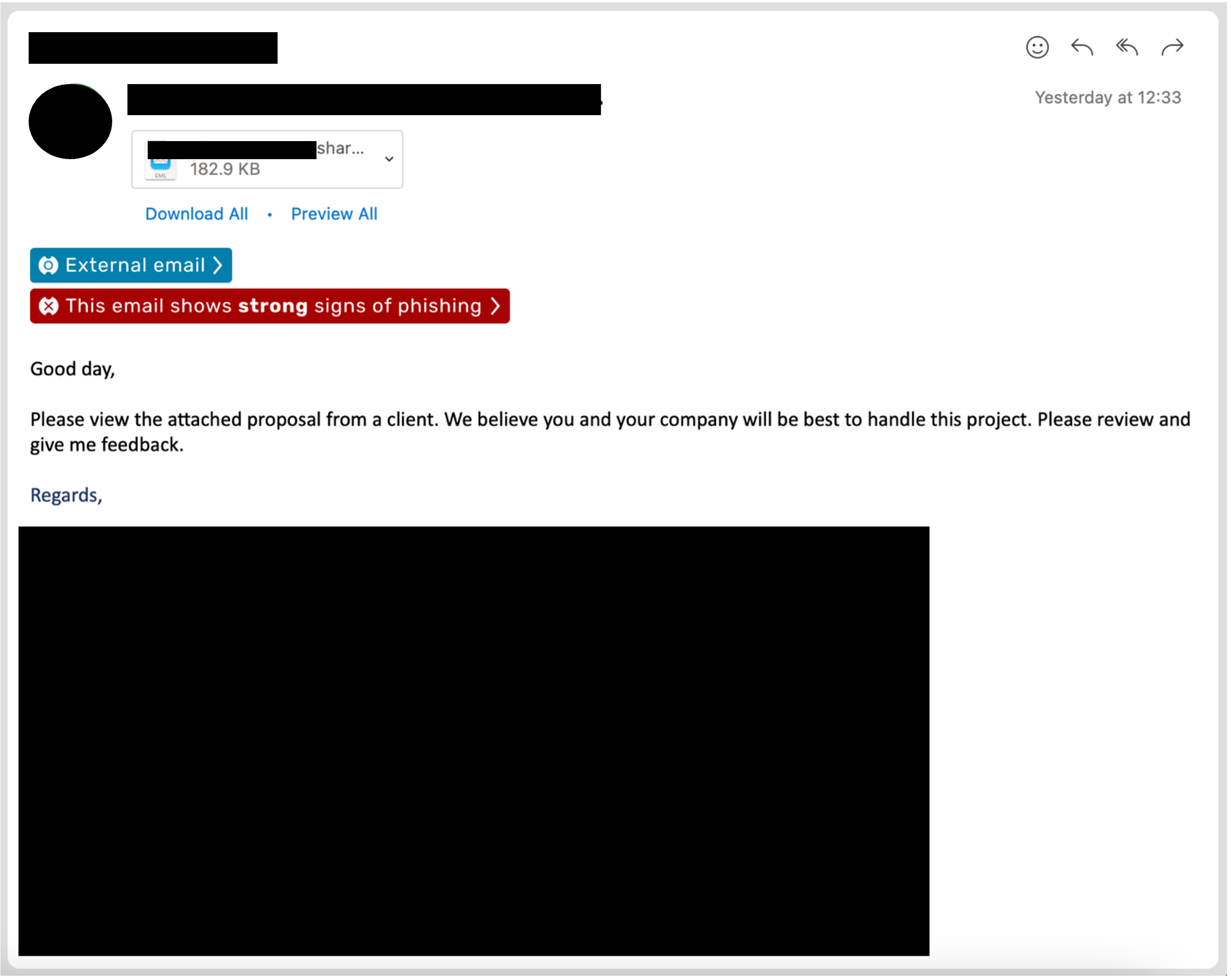
- Phishing email evades detection from our 3rd party Secure Email Gateway
- Phishing email showing strong signs of phishing lands in a number of users' mailboxes at the same time with all users on bcc
- The email contains an attachment for a proposal that needs to be reviewed (the hook)
- The attached email is a OneDrive file share which is encoded with base64 and contains a link to a OneNote notebook hosted in SharePoint
- User observation - we're usually greeted with 'Hi chaps', never received a 'Good day' before...
[screenshot of email]
[screenshot of attachment]
Time to investigate! 🧐
- We were able to click on the interactive Egress Defend HTML banners to learn more about why this had been flagged as a phish
- This revealed the following information:
- Non-specific email addressing – there is no ‘to’ address and everyone has been BCC’d. This is commonly used to send to multiple users from a list.
- File sharing links are contained in the email.
- The email has suspiciously little content.
- The links in the email look suspicious and are likely to be hiding their true destination.
- The email contains suspicious attachments.
[screenshot of Egress Defend learning page below]

What happens when you click? (don't try this at home kids...)
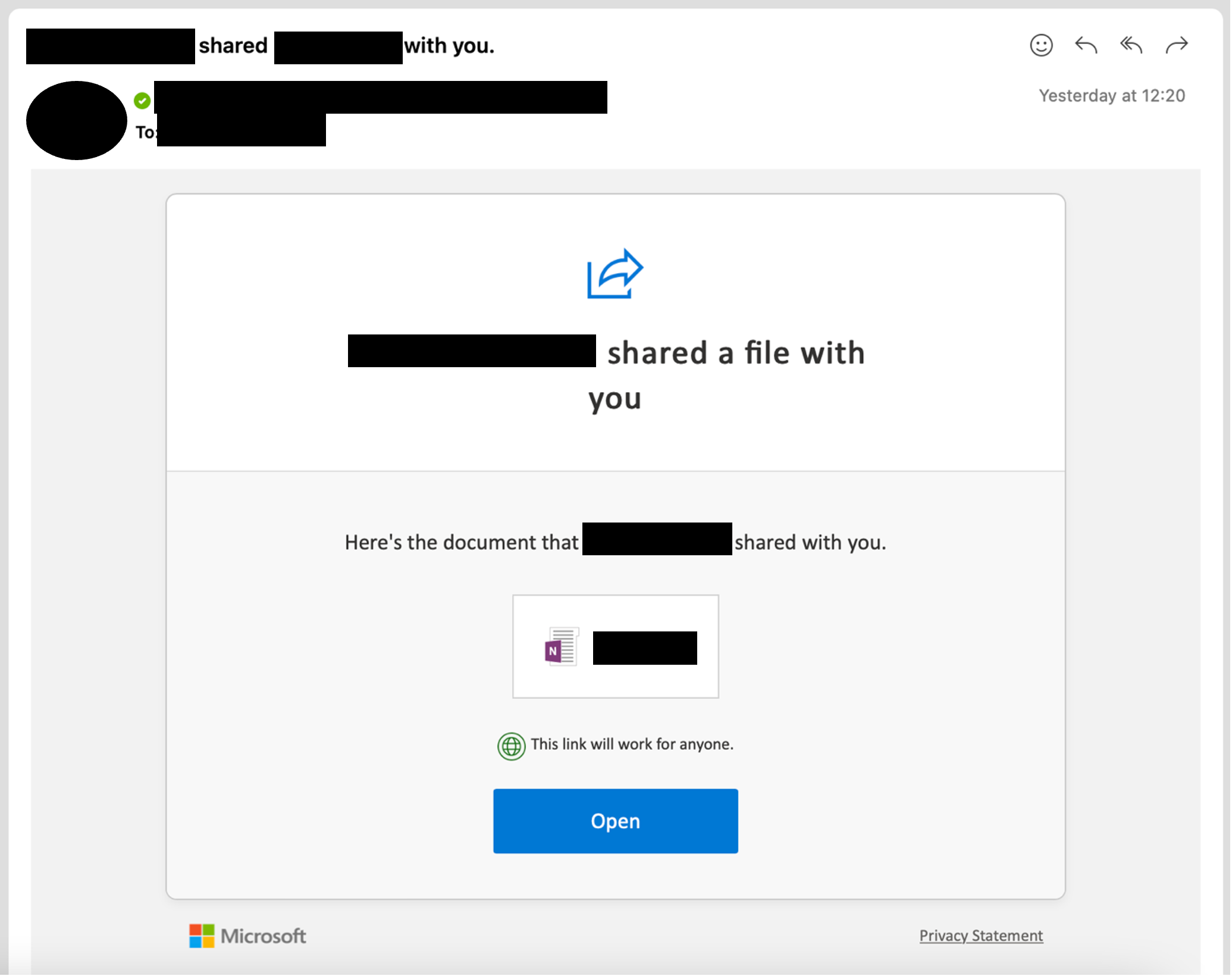
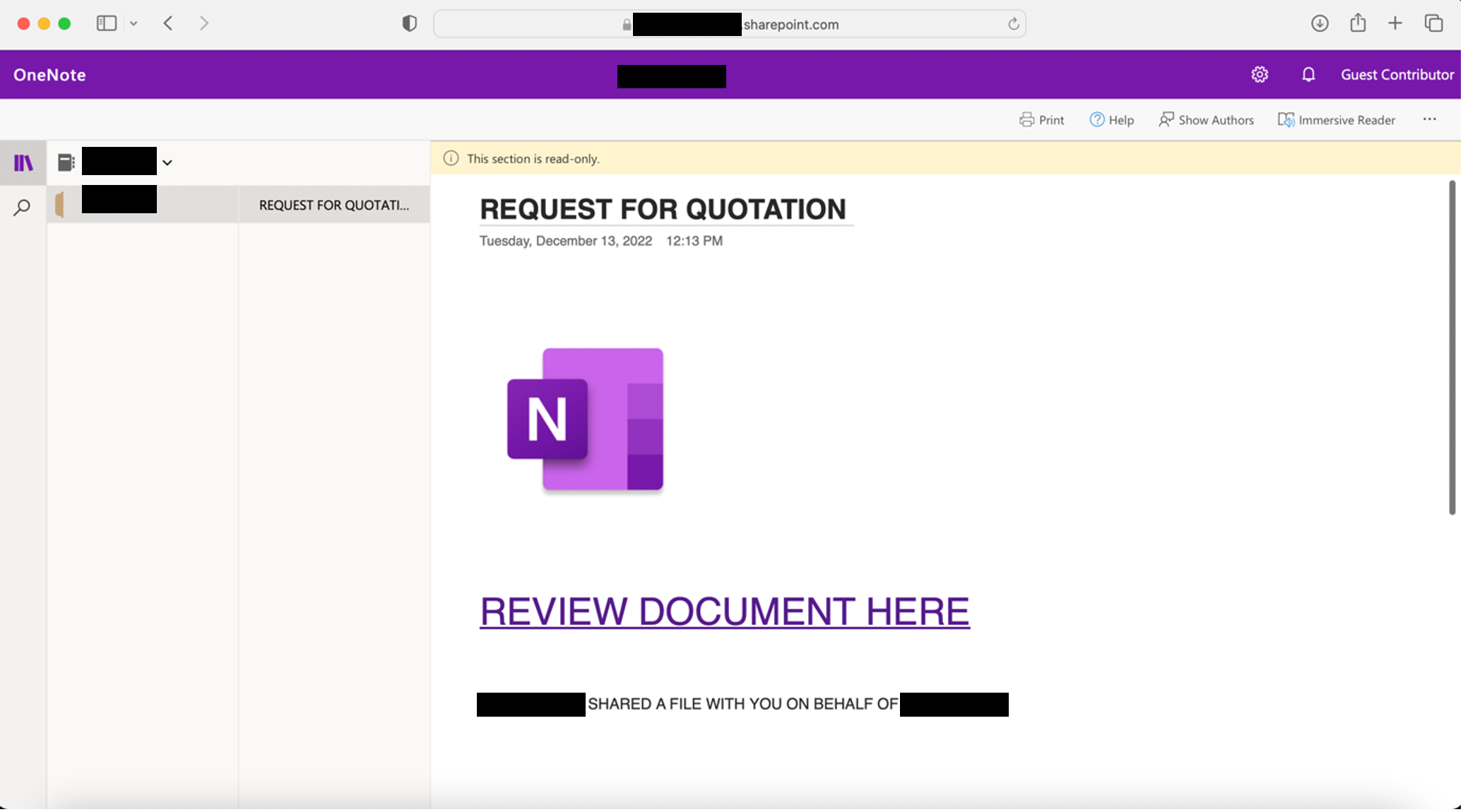
- The OneDrive file hosted in SharePoint contained a link to another site:
[screenshot of OneNote landing page below]
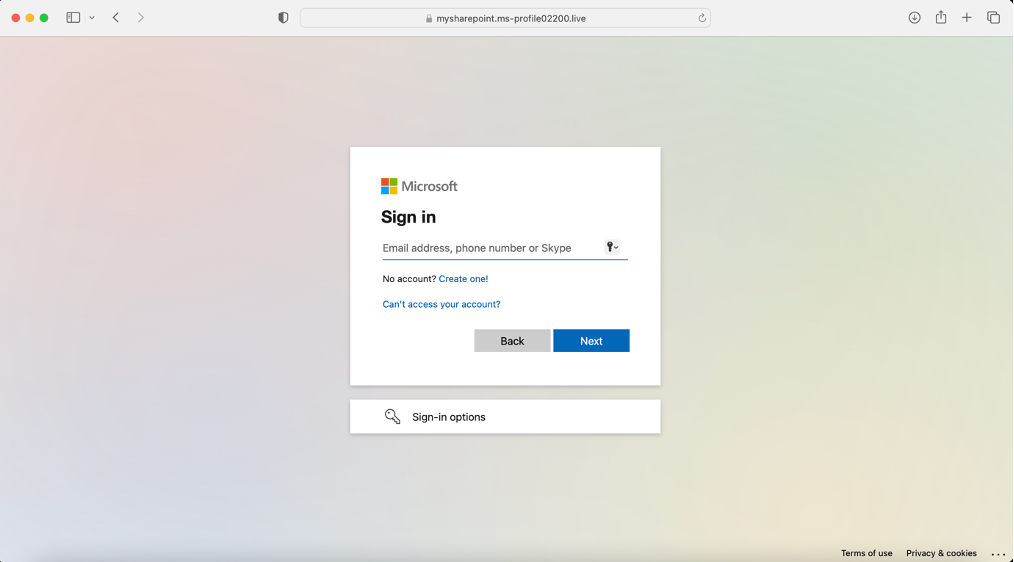
- Which takes you to a Microsoft 365 (and pretty convincing!) credential harvesting page
Fun Fact: A quick look up found that the domain was only registered on Monday! (the day before the phish was sent + received)
[screenshot of credential harvesting page]
The de-brief
This was a sophisticated one! You have to ask yourself, would an average user at any point throughout the timeline of this attack have been able to spot that it was a phish?- It evaded detection from the SEG
- The subject matter triggered our interest
- Who knows what would have followed from the credentials being harvested!
- We did phone our contact who confirmed their account had been breached and they are working on incident response
Our recommendation: Educate your users in real-time!
It's saved our bacon in this example and made our users think twice.
Static CAUTION: This email originated from outside of the organization. This message might not be safe, use caution in opening it. If in doubt, do not open the attachment nor links in the message. email banners are no longer effective.
User's click next, next, next, next, complete on dried up, generic online training content.
Cyber criminals are forever changing their approaches and it's time we do too.
Interested to learn how Spear Shield and their customers are able to spot sophisticated phishing attacks that are able to slip through the net?
Spear Shield are currently running a FREE Email security assessment that can help you identify:
- Total number of Dangerous and Suspicious emails detected landing into employees inboxes throughout the engagement
- Insight into the top types of phishing emails your organisation is receiving
- Insight into the top types of payloads being used in the phishing emails your organisation is receiving
- Insight into your Supply Chain Health (DMARC status of inbound emails)
- Insight if there are live phishing attacks sat in employees inboxes that can be remediated together
- Phishing Simulation results (with and without an ICES solution implemented)
- Previous caught user analysis breakdown
- Insight into how many users were stopped in their tracks at the link advisory page
- Insight into the reporting heroes in your organisation
- Insight into what device type your employees are engaging business emails on. (mobile, PC, both)
- Consultative recommendations for security best practice
If you'd like to learn more, you can visit https://www.spearshield.co.uk/human-activated-risk or contact the team today:
01473 948980
About Spear Shield
Here at Spear Shield, we are continuing to invest in our goal to create one of the most cyber-secure client communities in Suffolk, East Anglia and across the UK.
Our approach is to work closely with IT teams and business leaders to help identify cyber risk, understand core business drivers and challenge the conventional approaches to legacy cybersecurity strategies to enable our customers to exceed their cybersecurity goals.
Spear Shield has a portfolio of award-winning cybersecurity solutions and services that we align to enable our customers to be able to solve even the most complex and advanced cybersecurity challenges.
The team at Spear Shield specialises in:
- Mitigating the risk of social engineering attacks and human-activated cyber risk
- Real-time asset discovery, device security and compliance
- 24/7 Managed Threat Hunting and proactive Incident Response
If you would like to learn why organisations are choosing to secure with Spear Shield, please do contact a member of the team to arrange a confidential conversation today.
The team has several year's experience working within both the private and public sector, have a very consultative approach and would welcome the opportunity to learn more about your organisation.

Max Harper
As CEO and Co-Founder of Spear Shield, Max Harper is focused on building one of the most cyber-secure client communities across Suffolk, East Anglia, and the UK. He works closely with business leaders and IT teams to understand what really drives their organisations – then helps them challenge traditional cybersecurity approaches, rethink their risk strategies, and implement solutions that actually make a difference without impacting user productivity. Max’s goal is to ensure customers can articulate risk confidently, demonstrate value internally, and exceed their cybersecurity goals – with a trusted partner by their side.